
protection
Protected Node per Node Type Settings
Node Type extension
The Protected Node module adds a field set to the Node Type form that you edit under:
Administer » Content management » Content types
These additions are explained in detail below.
The main reason for adding this feature is to avoid seeing the field set on all the node edit forms. With this feature you can hide the form on all the node types that you will never protect with a password.
Protected mode for nodes of this type
This option let you choose how this node type handles the Protected Node capability.
Never protected
This means this node ...
Protected Node Password Form
Protected Node Password Form
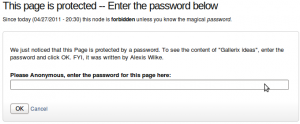 Once a node is protected, users who cannot bypass the password are sent to the password form (see image on the side.)
Once a node is protected, users who cannot bypass the password are sent to the password form (see image on the side.)
The password form is very simple. It includes one field for users to enter the node password and an OK button.
When the browser of the user sent us a referrer, then the Protected node module adds a Cancel link back to that referrer. Using the global settings, you can force a Cancel link to always be there. When no referrer is available, the Cancel link will send your users to your home page.
The title, information, description and title over the
Protected Node Global Settings
The protected node module has global settings found under:
Administer » Site configuration » Protected node
Protected node Statistics
The page starts with statistics to let you know how pages are protected on your website. All the counts include published and unpublished content.
- Total nodes — the total number of nodes on your website
- Unprotected nodes — number of nodes that do not have a password
-
Protected nodes — number of nodes that are current protected by a password
- Showing title — number of nodes showing their ...
Protected Node Permissions
The Protected Node module adds permissions to define who has the right to make use of the password feature.
- access protected content
This is the basic access permission for users. Users who are given this permission can access a protected node as usual, except that they need to enter the password to handle the node.
This is true whether they want to view, edit, delete the node.
- bypass password protection
Users with the bypass permission can access all nodes that are protected without having to enter the passwords. This is very handy for website administrators and
Protected Node (The Drupal module —)
The Protected Node module is used on websites where some pages need to be password protected. This is different from asking someone to create an account and often seen as much more user friendly, although in terms of protection it is quite similar.
If you've seen photo websites where you can go to an album but have to enter a password to see the photos, that's one example how this module can be used.
The module adds a field set in the node form to let authors enter a password.
The module has many options that are rather tricky to use so this documentation tries to explain what you can do
To Do List Global Settings
Global Settings
Global settings are found under Administer » Site configuration » To do list (admin/settings/to_do).
Only To Do List administrators can edit the Global Settings.
Insert Node Known Issues
The following are problems that have not been resolved and will probably not be.
Tag not transformed
At times, you enter the tag as in [node:123 cck=title] and it is not converted by the filter.
There are 3 common reasons for this to append:
- You did not select the filter in your Input formats;
- You did not select the format that uses the filter in that node; or
- There is a syntax error in the tag.
The 3rd one is certainly the most likely explanation once you made sure that the filter was effectively selected for that node. In many cases, it will be the missing ...
Protect
The protection tag is totally useless. The SWF format is an open format, otherwise how would you have so many players and tools to work with SWF movies? Thus, you can pretend to protect your movies, but anyone with a simple binary editor can transform the tag and make it another which has no such effect. Also, swf_dump and some other tools (such as flasm) can read your movie anyway.
For the sake of defining what you have in each tag, there are the protection tags fully described.
According to Macromedia, you can find some free implementation of the MD5 algorithm by Poul-Henning Kamp in ...
DefineSound
A DefineSound tag declares a set of samples of a sound effect or a music.
The sound samples can be compressed or not, stereo or not and 8 or 16 bits. The different modes are not all available in version 2, although the same tag is used in newer versions with additional capabilities.
The f_sound_is_16bits is always set to 1 (16bits samples) if the samples are compressed (neither Rawnor Uncompressed).
The f_sound_rate represents the rate at which the samples are defined. The rate at which it will be played on the target computers may differ. The following equation can be used to determine the ...
Our 30 Day Money-Back Guarantee
Our goal is to offer great service with effective, robust software. We are so confident that you will enjoy our products that we offer a 30-day money-back guarantee.
If you are dissatisfied with a software purchase, contact us within 30 days; if we can't make it right, we will assist you in deleting the installed software and refund your purchase price. To get your refund, please log in to your account and fill out our secure return form with an explanation of your dissatisfaction. We will refund your purchase price upon receipt.
Ensure your protection with our guarantee by reporting any ...
